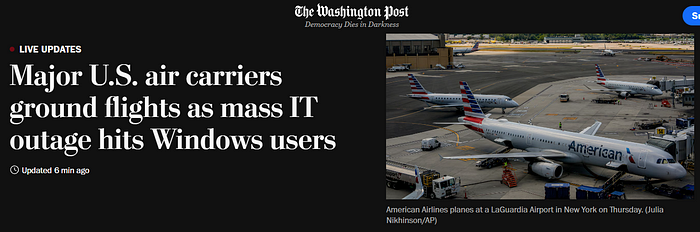
Today the Washington post runs a live-update feed and titles as breaking some ICT news on a bug — not a cyber-attack! — that affects way too many people dealing with a desktop computer today at work:
“Several major U.S. airlines — including American Airlines, United and Delta — grounded flights early Friday due to a technical issue impacting IT systems, as mass outages disrupted airports, banks, broadcasters and businesses around the world. Microsoft said it was aware of an issue impacting Windows programs running cybersecurity technology from CrowdStrike.”
Live updates — The Washington Post
Now, while things are getting fixed up there, in the cloud, I have a suggestion for all of us who have ever worked on large scale and mission-critical systems.
Let’s all take a deep breath and get prepared to pose this question to our colleagues:
Is the cybersecurity industry really aware of its weaknesses, or are they fooling us with marketing and off-shelf products, keeping the door closed to 20 years of innovation on E2EE, decentralization and resilience?
Or, in other words: are organizations really spending money on securing their services, or that dosh ends up into a huge corporate black hole of hidden misconducts, ready to shoot us into reality at every glitch?

We’re in 2024 and “enterprise-grade” systems are cloud central nightmare, no lesson was ever learned about resilience and decentralization. An auto-update mechanism of some “intrusion detection and response” security closed-source software blocked Windows operator terminals worldwide, causing major outage on way too many computers people use at work.
Meanwhile huge spending is directed towards the cyber-security industry and most of it doesn’t adopts any scientific method to verify what is being put in place and how. Let alone the fact we are calling “secure” some software that is closed source, and is lacking quite some “due diligence” in ICT terms, lacking proper testing on its continuous integration pipeline that is automatically broadcasting live-updates worldwide, which is exactly what is causing this pain.
Solutions to this mess cannot be patches. We need systemic change in the cybersecurity industry.
Including solutions as the adoption of open-source software everywhere, while raising the bar of its quality assurance and transparency of operations, as recommended by the European Cyber Resilience Act:
We need resilience!

The heart of this issue is the delegation of responsibility for risk and change management of critical infrastructure systems.
The centralized and automated management of an individual organisation in charge of operational reliability is directly responsible for deploying a component without a risk assessment process and change management control point. The incident yet again reminds us of the famous IBM manual statement.

Let me conclude stating all my solidarity to the technical operators who are involved — boots on ground — to prevent huge disasters this may be causing in numerous hospitals, airports, city-halls, etc. I really whish that whoever is taking the ICT supply-chain decisions in your organization manages to realize what this worldwide BSOD sensation in 2024 really means.
You can visit my homepage with recent publication and projects at jaromil.dyne.org.
If you need developers that can secure your project infrastructure, contact The Forkbomb Company at info@forkbomb.eu.
Ciao!