A while has passed since my last “lockdown diary” posts, where I’ve done my best to share some reflections on what is happening and how tech is being used to alleviate our lives in Corona times — or perhaps hypnotize us.

Recently we face plans by the European Union to develop a “vaccine passport” to enable mobility of vaccinated subjects, something that really seems on top of the EU agenda and even in the UK, after spawning an avalanche of unwieldy and risky software applications in the US.
Disaster in the making
“The physical manifestation of the mythical “land of vaccine” might as well be on the barren archipelago of Nova Zembla, once the site of nuclear testing, cruise ship sinking and likely forms the derivation for the word zemblanity: the act of making unhappy, unlucky and expected discoveries occurring by design. (Adam Burns)
For a critical start this article is a good reference:

I think harryhalpin makes an important point, on top of well referenced technical analysis, to conclude that:
“This form of digital identity runs counter to privacy, opening the door for a new form of identity totalitarianism where every person must be identified in a database.”
Well before this conclusion the article explains in good detail what is wrong with current technical “standards” drafted by W3C for distributed identity (DID) verifiable credentials (VC) and the likes.
I don’t mean to diminish historical considerations on the dangers of identification campaigns in society. But it is clear to many of us cryptographers and computer scientists that current standards built around the idea of a “Self Sovereign Identity” (SSI) are not fit for the purpose: they are incomplete and they leak too much information.
Some even argue that the concept of SSI is a dystopia.
At last, for the sake of completeness, let me mention that there is no scientific proof that a vaccinated person will stop spreading the infection, also considering asymptomatic spreaders existed well before the vaccines did. But let’s please ask a medical expert before debating this, OK?
Zero-Knowledge proof and disposable identities
It seems that despite all the good reasons not to do a “vaccine passport” the plan may go through, because…???
Here comes my next big frustration then, after decades of research and development on privacy-preserving technologies: very few people in charge of decisions seem to understand a flying sausage about Zero-Knowledge proof.
It feels like we work for “systems designed to impede risk that are then activated by key actors to construct their own misfortune.”
(Organizational Zemblanity, 2016)
In the desperate attempt to make things a little better then I’ll hint how a “disposable identity” can be implemented using a strange thing called science and free and open source software that is easy to use.
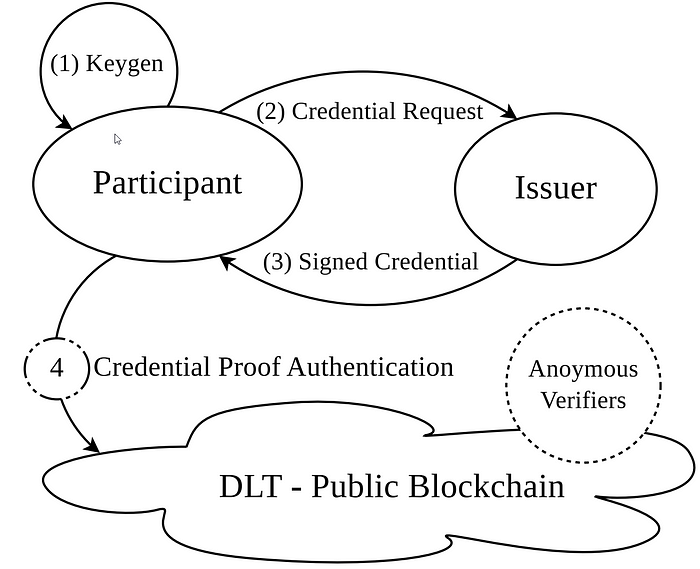
The concept is simple: the only known subject here is the “Issuer” (the authority releasing the credential), no other identity is disclosed. The “Participant” requests (2) and obtains (3) a signed credential along with the vaccination, storing its keys locally (1). This is done only once. Then the Participant is able to show a proof of vaccination that changes every time (is not traceable), but can be verified by anyone even not knowing other details about the participant: verifiers just need to know the Issuer.
Here below another post where I explain more in deep the REFLOW signature scheme and links to the paper pre-print, free to download.

This authentication system can be easily implemented using the free and open source software Zenroom that we developed for the EU H2020 flagship project DECODE: it has bindings to javascript, Python, Java and Rust, it can be easily embedded in any mobile device (Android or iOS) or browser (Wasm) and is programmed using human-like language.

For an online demo go to ApiRoom.net and select the “Zero knowledge proof flow” among the examples. Scrolling further down a bit one may notice there is also a W3C verifiable credential example, where the credential signature is done with an old-school Diffie-Hellman sign/verify process that I do not advise to use for vaccine passports.
Which is (of course!) the only thing implemented in a “W3C standard” that, as Harry points out in his critique, has not even specified how deterministic serialization should be done on data objects.
Anyway.
I do not advise to use vaccine passports at all.
But if they really have to exist then please! for the love of humanity lets avoid creating a privacy nightmare or even worst using proprietary software written in pesky ways and marketed around at the price of our Freedom.
If you think I’m exaggerating, then search for “qrcode vaccine passport” in your own language and see what sorts of scams you’ll find.
If you read until here and still want to do a vaccine passport then please consider one exists already:

Tune in to the discussion 💬
(These services are bridged: join your favorite and reach them all)
🗨️ Matrix
🗨️ Telegram
🗨️ Discord
Support Dyne 🫱🏿🫲🏾
🪙 Bitcoins: bc1qz9wz2f9swcefra2tfrhk4fx49evqsv03m9nx4l
☕ Ko-Fi
🍴 Github.com
🧁 LiberaPay
🍥 Patreon.com
Follow Dyne.org 🗞️
Social Media everywhere!
🐘 Mastodon
🎬 Peertube
🐭 Lemmy
📸 Instagram
🐦 Xitter
👔 Linkedin
🪞 Facebook
✍️ Medium