Independent feedback on the dangers of the current EUDI implementation.
Contents
- Introduction
- What EUDI should be
- 1: Fairness
- 2: Privacy
- 3: Security
- 4: Scalability
- 5: Obsolescence
- 6: Methodological
- 7: Stakeholder Engagement
- Conclusion
Introduction
The EUDI architecture reference framework (ARF) is built on the eIDAS2 specification, and its implementation act has been recently approved by representatives of EU’s member states. The European Commission has just ratified its adoption.
What EUDI should be
I take this stance because I want Europe to be excellent to all its citizens. We should develop our technological solutions following a human-centric approach grounded on principles of privacy, fairness, and inclusion.
The motivation behind EUDI is that of achieving strategic autonomy for our public and social services, but its realization goes in the opposite direction, effectively putting in the hands of mobile OS manufacturers core interaction channels with the institutions governing our society.
As it is today, EUDI has lost my trust, and it does not deserve yours either.
I will do my best to enumerate the reasons.
Fairness issue
What EUDI’s entertaining announcements often omit to say is that this system will not just issue but also revoke the digital identity credentials of European citizens. And revocation is an extremely delicate function with huge fairness implications. In the words of the European Commission EUDI will make us “enjoy” secure cross-border identification for services like:
🚗 Digital driving license
🩺 Access to medical prescriptions
📧 Digital signature
💳 New bank account
🧳 Travel documents
Considering this I cannot stress enough how important the governance of a revocation mechanism is. In EUDI’s implementation today this is a single point of failure where issuer corruption can cause huge damage to persecuted minorities and targeted subjects: it delegates the revocation issuance to a single entity instead of requiring more approvals by a quorum of stakeholders.
This creates a fairness problem that EUDI refuses to contemplate.
In other words, as it is now, a single party can interdict a person to access all these services. This is not good, and it does not have to be this way (technically speaking): we have shown that it can be done in a more resilient way, requiring agreement on the matter by multiple parties, in a paper we published.

open access: https://arxiv.org/abs/2406.19035
Where we demonstrate it is possible to have a multi-stakeholder governance of revocation issuance.
Privacy issue
EUDI will endanger the privacy of citizens using it because of the choice of weak cryptography algorithms that may leak information in certain situations, for instance in case of issuer-verifier collusion. The Cryptographers Feedback document explains this in detail: world-class researchers wrote and signed this document expressing important concerns on the cryptography adopted and its level of privacy, but EUDI acknowledged it without solving any of the problems raised so far.

A year before this feedback also the European GSM Association has issued a worrying response to the EUDI plans, and the concerns it raised back then are still actual

There are of course solutions to the privacy issue, but they aren't simple. In this other article I dig deeper into the privacy issues of EUDI, how they can be solved by the adoption of zero-knowledge tech, but also the pitfalls of adopting such cryptography in the wrong way:

Security Issue
The security model of the EUDI wallet component relies on the Trusted Execution Environment (TEE) layer provided by mobile OS manufacturers: it gives up the use of advanced cryptography to be compatible with an API controlled by an oligopoly of foreign companies. This hands over the governance of EUDI algorithms, and potentially the control and monitoring of all transactions, to Google and Apple, who are now leading every session of the implementation acts.
As if this would not be enough of a disaster, most EUDI “experts” involved seem to ignore the fact that mobile TEEs are not secure at all!

All big players in the identity industry have since long been aware of exploited vulnerabilities in mobile TEEs and do not rely on them, for particularly good reasons!
Following EUDI ARF specs, wallet implementations should use Hardware Security Modules (HSMs) whenever found on mobile devices, a measure to defend wallet holders from side-channel attacks. The problem with this is that there are only a few mobile phone models in the world with certified HSMs, all extremely expensive high-end models. This also casts a shadow on the legitimacy of double standards for security, with a situation in which nation-states provide insecure infrastructure for citizens who cannot privately afford secure means to access it.
I believe that, if the European Blockchain Service Infrastructure (EBSI) serves its purpose, then we can solve the problem with a decentralized software approach that preserves our privacy and is more resilient to attacks. The advantage of such a solution would also be that we can update it without depending on mobile OS manufacturers. We demonstrated how to do this already on various use cases using Zenroom, a project born out of research funded by the European Commission.
Scalability issue
According to its ARF the EUDI system is not scalable: its use of antiquated cryptographic signature algorithms will impose the issuance of multiple attestation copies for each credential.
“This solution is not ideal: it introduces extra load for attestation issuers as well as additional complexity in the software. When using ordinary signature schemes such as ECDSA to sign the attestations, we see however no practical alternative.”
- NL Wallet Design Considerations

EUDI partially solves some of its privacy issues at the cost of increasing operational complexity, to a degree that will quickly become unsustainable at large scale.
See also the Findynet Cooperative feedback to eIDAS implementation regulation:

However scalability issues are fathomable, and there are solutions to them. It may seem that the increase of public sector’s technical debt is among EUDI’s undeclared purposes.
Obsolescence issue
The EUDI specifications are not concerned at all about Quantum Safety and makes no recommendation to face Quantum threats. This negligence makes EUDI already obsolete today.

National Security Memorandum on Promoting United States Leadership in Quantum Computing While Mitigating Risks to Vulnerable Cryptographic Systems – The White House
Quantum-safe cryptography, also known as post-quantum cryptography (PQC), refers to cryptographic algorithms designed to be secure against attacks by quantum computers, which are foreseeably possible within the next 10 years. This makes quantum-safe cryptography especially important for long-term credential systems like ID cards or driving licenses: as quantum computing technology advances, the risk of quantum attacks on current cryptographic systems increases. This means that adversaries with access to quantum computers can use credentials signed today to steal private keys in the future.
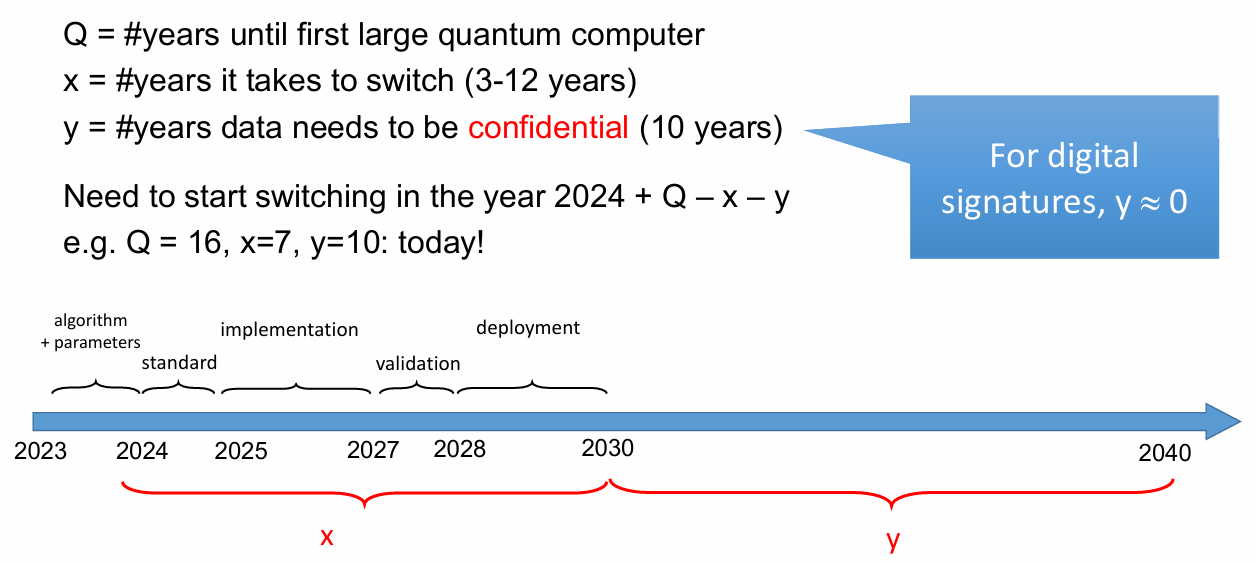
European member states should ensure that their data remains secure both now and, in the future, preventing obsolescence and maintaining the integrity and confidentiality of sensitive information, by incorporating quantum-safe cryptography into authentication systems.
Methodological issue
There is a fundamental methodological problem in the way the European Commission’s Directorate General for Communications Networks, Content and Technology (DGCNECT) drives the development of EUDI.
When working on a system that is liable for a literally everyone's privacy and can be subject to cyber-attacks, abuse of power, and what not, the first step should always be that of establishing a threat model which should underpin and certainly precede the inception of an architectural framework.
A threat model is a critical component of any project focused on security and privacy, it serves as a foundational framework that identifies, evaluates, and mitigates potential risks and attack vectors, to anticipate and address security issues already in the architectural design phase. Threat models are there to provide an objective and scientific assessment of priorities that cannot be improvised by project managers, but are made by interdisciplinary groups of stakeholders focusing on security: they drive the decision-making process with insights that help everyone understand the potential impact of various threats, the effectiveness of mitigation strategies adopted, and helps prioritize security efforts on certain aspects and allocate resources on certain tasks.
Regulatory frameworks and industry standards require a threat model as part of their security protocols not just to ensures compliance but also to align with best practices in security management.
To mitigate this negligence, I am volunteering as facilitator of the Threat Model Community group at W3C (TMCG) and co-chair of the Security Interest Group (SING)

Our first focus at W3C SING has been digital identity wallets, working with an interdisciplinary group that also includes experts from different backgrounds. We work to contribute a document that can fill-in for this omission in EUDI, despite the fact it may be already too late: such a project should work on threat model analysis at its inception!
Stakeholder Engagement
The EUDI development process seems to disregard feed back from experts, including cryptographers and security researchers, including the feedback I've mentioned in this document. Even worst, it doesn't even care to involve anyone out of the engineering field or business sector of companies profiting of identity services, so this implementation has never been informed by researchers from humanities and social sciences.
A lot of passion seems to be invested in announcing EUDI as a new shiny digital tool to the European public, to the point the project clearly abuses marketing rhetoric above levels of alert. It is running biased advertisements across social networks, and running presentations at roadshows, without any critical notion of the impact and role of such a technology in society.

This is not the way it should! European society underpinnings include secularized principles of rationality, an epistemic process of falsification, and openness to criticism and different views.
The marketing of EUDI’s implementation is far from these principles and makes Europe’s voice closer to blatant propaganda techniques used by our enemies to enslave their population under totalitarian regimes. I hope to be wrong in my interpretation, but right now this is how I feel every time I see a LinkedIn post on the EUDI fanfare: as people have already commented, this is all very creepy.
Conclusion
Unfortunately, EUDI as is today presents big problems and disregards criticism, warnings, and requests to review technical details, with results that harm the fairness of the system and the privacy of its participants, also limiting infrastructure security and scalability.
Citizens will be free to voluntarily adopt EUDI-compliant wallets available in each national member state, but this does not solve the problem that EUDI exists as a flawed system. It also gives no warranty about never becoming mandatory in the future.
I really hope that colleagues reading this declaration open to criticism and engage a more fruitful exchange with the cryptographic and security community. Together with other experts in the fields we have promoted open dialogue and a process of interdisciplinary and multi-stakeholder inclusion through recent initiatives like the Security Interest Group (SING) at W3C, in which I’m serving as facilitator for which I’ll do my best to welcome different opinions and run security analysis of verifiable credential schemes proposed. I will always be serving Europe’s interests with my expertise and always be open to cooperating to improve things if given the chance. One recent thing I'm contributing is this review of another privacy-preserving solution.

All problems I have listed here have solutions, but they may take time to solve, time that may not fit the plans of bureaucrats busy with matching overdue deadlines and incapable of comprehending the techno-political implications of this rush.
What worries me the most then is the condescending attitude of experts involved in this process, some euphorically, almost hysterically celebrating EUDI as a success, others silently witnessing the unfolding of what I predict to be an embarrassing disaster for Europe, or in the very best case an aborted project who has costed already more than a hundred million euros, and still counting.
Today we must understand the collective memory of Europeans will define EUDI’s initiative only after ripping the Maya veil of its marketing rhetoric, celebrative roadshows, and career opportunities. As it stands today then it will appear as a miserable show of false assumptions, ignorance and short-sighted choices marking a turning point in history for the erosion of Europe’s digital integrity and sovereignty.
Who am I?
My name is Denis Roio (Jaromil.dyne.org) and I know very well the subject after more than a decade leading developments for the European Commission, being the co-founder of the Italian Society of Cryptographers “De Componendis Cifris” and of Forkbomb BV. Months ago, our team working for the NGI TrustChain fund published the first 100% free and open-source EUDI-compliant implementation (DIDroom) complete with wallet and verifier apps already available on Android and iOS stores, as well as a complete issuer dashboard available in both SaaS and on-premises. We are now launching our new product, the most extensive interoperability test framework available for identity applications (Credimi) well placed to become the trust-pilot of identity in Europe.
What I am writing about here may well be against the commercial interest of our company, while motivated by ethical and deontological values.
This article has been published as a peer-reviewed panel (ID 361) in the acts of the STS Italia 2025 conference "Technoscience for Good: Designing, Caring, and Reconfiguring" for Panel 76 "Where Sociomateriality Lies: Re-Thinking the Synergies Between STS and Information Infrastructure Studies in the Age of Datafication". Contact me for more information about Science and Technology Studies in Europe and why it matters for EUDI.

Yours faithfully














