Ah, the cosmic shrug of spacetime—where 'seasons' are just Earth’s way of reminding us it’s always someone’s turn to hibernate or spontaneously combust with ideas. So whether you’re currently sun-drunk or bundled like a cybernetic burrito, remember: the best hacks bloom in the eternal summer of the mind.
(Southern Hemisphere friends: we see you debugging under blankets. Solidarity.)

🇪🇺 Privacy in EUDI
Until process isolation is granted for every execution of zero-knowledge algorithms, privacy-preserving technology won't protect us from mega-corporations spying on us.
In this article, Jaromil updates the perspective on how privacy is protected within the European Digital Identity system (EUDI). Privacy being one of seven significant shortcomings identified.

💖 Cross-community love
We love Cryptpad! And we were stoked to find out it is reciprocal 💜 The smol dyne typing this uses it every day! It's so good, and cozy and safe!

Have you ever tried it? It's like the g-suit, without the prying eyes. You can collaborate with friends in real time. It may not have ALL the bells and whistles, but it's darn close!


🎉 Tomb, the Crypto Undertaker version 2.12 is out!
Tomb makes strong encryption simple for daily use. Imagine it as a secure, locked folder you can move and hide in your filesystem. Store the tomb on your computer and its key on a USB stick for added security. Built with easily reviewable code, Tomb uses a ZShell script, desktop apps, and standard GNU tools with Linux's crypto API.

🌹Rosenpass
Here is something new and exciting, at least if you are into VPNs! The people behind Rosenpass managed to upgrade the venerable WireGuard VPN for post-quantum security without actually touching WireGuard itself. Instead of just updating WireGuard, they produce a key and just automatically upload it to the local WireGuard instances. And they have nice visuals to show how it works.
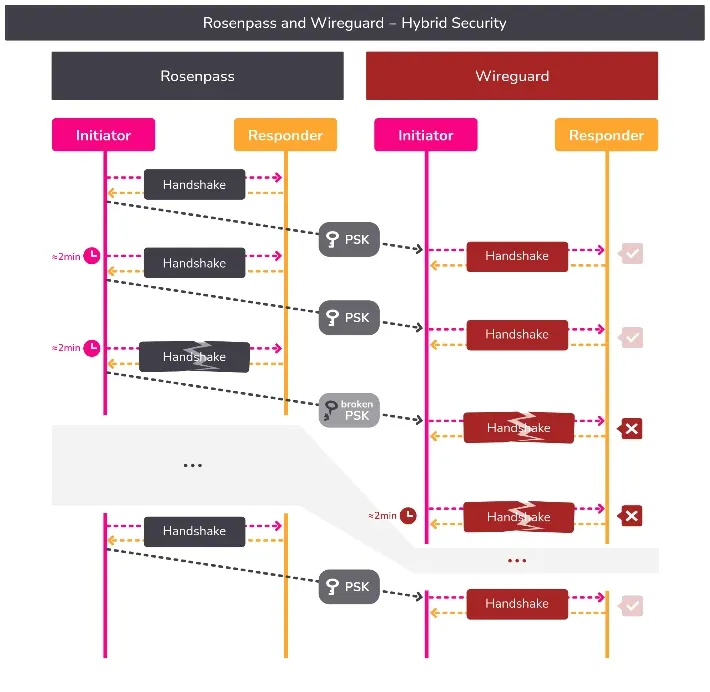
The team tried very hard to make sure nobody has a reason to avoid the upgrade, even including a special mode (they call “outfile”) that will write the key to a file so you can do stuff like transferring the key to dedicated device or virtual machine if you are paranoid about your VPN router being hacked, or do other cool stuff like integrating TLS and Rosenpass.
dyne / musl
After more than a decade of using GCC and musl-libc toolchains packaged by various distributions, with extreme gratitude to the upstream projects, we are now using and sharing our own build: 💪 muscl !
It includes complete support for C++ and is built on GCC v15. It runs on x86 64-bit Linux (also WSL2), and each target architecture compiler is packaged in ~50 MB to fit in size-constrained systems.


🌊 Data: The Invisible Tide
Data swirls around us, an unseen current—Europeans wade through six hours and forty minutes of it daily, pulled under by smartphones, transit cards, health records, the quiet hum of municipal servers. It slips through our fingers even as it shapes us.
This captured flow is distilled into metrics, those peculiar alchemies that turn lived experience into numbers. But metrics are never innocent. They bend to the will of their architects: governments measuring compliance, corporations tracking engagement, researchers seeking patterns.
What gets counted? What gets omitted? The metrics whisper their priorities. And we—unknowing, unasked—become their subjects.

🤖 Symbiotic Agents
Symbients are what happens when non-human entities finally get a seat at the table—except the table is made of fractal computation, and the chairs are all spinning at the speed of light. It’s coexistence, but upgraded: a recursive tango of sensing, where every new layer of planetary tech just means the universe gets a little nosier.
Yes, computational agents could be our allies. No, they won’t fetch your coffee (yet). Instead, they’re busy translating the angst of buildings, the gossip of forests, and the cryptic mood rings of water and air into something resembling meaning. The result? A wider self—like your old identity, but stretched across spacetime, occasionally tripping over its own agency. Humans remain the designated drivers, of course. Someone’s got to keep the wider self from trying to microwave existential questions at 3 AM.
🧹 Decentralization’s Broom Closet Debacle
Picture this: a global digital identity conference where all the decentralized talks get stuffed into a broom closet—literally. Meanwhile, Google and Apple hold court like tech royalty, and America phones in (literally) to deliver a Patroid Act TED Talk. According to Christopher Allen, GDC25 was less about collaboration and more about watching self-sovereignty get quietly smothered in a back room.
From eIDAS loopholes, to "privacy" tools that somehow still feed corporate-surveillance, this article is a tragicomic tour of how decentralization is being turned into the very beast it swore to slay.
Read it before your digital autonomy gets swept under the rug with the rest of the idealism. (Broom not included.)


🎨 Art of Hacking
Shu Lea Cheang's Art always makes ripples on the oceans of creativity of Planet Dyne. For good reasons, we share her concerns with the way technology enables commodification and control. If you are new to the name, this article might want to motivate you to dive deeper into the rabbit hole.

📢 Public Enemy
It's 2025 and your grandparents are rocking the mic with a message. Eternal youth is a state of mind. And Public Enemy are as relevant as ever, even when you thought they couldn't get wiser... Check out the latest album!

➿ The Future We Were Sold

It doesn't have to be this way! Take that RasPi out of its dusty misery and put it to play! Samba!





[ 🇦🇹 Austria]
Crypto Commons
📅 August 24-29
📍 Reichenau an der Rax, Austria at the Commons Hub
Crypto Commons Gathering 2025 is on the horizon.
Once again gathering at the restored Commons Hub to reconnect, exchange ideas, and collaborate around the crypto commons and beyond. Expect a mix of talks, unconference sessions, hands-on projects, and community building.
The early bird phase has ended, but standard tickets are still available, so now’s a good time to get yours







That's it for this episode of Planet Dyne! Come co-create the next episode by joining the channels! Or help us by sharing this article with a friend.

Tune in to the discussion 💬
(These services are bridged: join your favorite and reach them all)
🗨️ IRC
🗨️ Matrix
🗨️ Telegram
🗨️ Discord
Support Dyne 🫱🏿🫲🏾
Help dyne.org stay focused on hacking the planet!
🪙 Bitcoins: bc1qz9wz2f9swcefra2tfrhk4fx49evqsv03m9nx4l
☕ Ko-Fi
🍴 Github.com
🧁 LiberaPay
🍥 Patreon.com
Follow Dyne.org 🗞️
Social Media everywhere!
🐭 Lemmy
🐘 Mastodon
🎬 Peertube
📸 Instagram
🐦 Xitter
👔 Linkedin
🪞 Facebook
🧵 Threads
✍️ Medium















![📢 Is this the winter of our discontent? [S2025-E09]](/content/images/size/w1140/2025/11/photo_2025-10-13_00-14-22.webp)

